Elevate the power of your work
Get a FREE consultation today!
In an increasingly regulated and privacy-sensitive environment, organizations can't afford a weak link at any stage of their data security strategy.

The challenge has been particularly acute as more employees (and their devices) have gone remote in record numbers, making it difficult for organizations to keep track of their IT assets.
A comprehensive approach to asset lifecycle management should include:
While data destruction is part of any good lifecycle management practice, it's easily overlooked. A 2021 study by researchers at the University of Guelph and the University of Waterloo found that one-third of online equipment resellers had erased data using insecure methods or not erased it at all.
So, how do you mitigate data security risks at every stage of the IT asset disposition (ITAD) process? And how do you ensure you're working with the right ITAD vendor along the way? Here's what to consider.
Responsible data management must include a disciplined approach to enforcing records retention policies and best practices. Businesses typically dispose of IT assets through remarketing, donation, or recycling. Regardless of the choice of disposition, it's the owner's responsibility to ensure that data is securely erased or destroyed.
Before IT assets can be retired or repurposed, devices must be comprehensively scanned and data thoroughly expunged before equipment leaves the premises. But erasing data isn't as straightforward as many people think. Deleting files removes them from directories but actually touches very little data. Similarly, formatting a disk drive deletes pointers to files, but much of the contents of the device can be recovered with special software. Even multiple formatting passes are not a guarantee.
Many third-party vendors are willing to repurpose or dispose of retired IT assets, but your organization should exercise caution when selecting a contractor. In many cases, the transition to a vendor is the first time equipment will leave your company’s control. Data destruction is the most important part of the asset retirement process and the easiest place for a vendor to cut corners. Responsible contractors should demonstrate that media erasure is conducted using overwriting software that complies with the NIST 800-88 standard. It should also provide audit reports and certificates that verify the data has been thoroughly scrubbed.
For assets that can’t be reused, a reputable vendor should provide proof of destruction and environmentally responsible disposal. They should also provide certificates of deletion, recycling, and destruction for every asset for internal audit and compliance purposes.
From the moment assets are loaded onto a truck they are vulnerable to compromise. A quality vendor should be able to demonstrate that your equipment is fully secured from the moment it takes possession until disposition is complete. And if you can’t send your equipment off site for security reasons, an onsite decommissioning option should be available.
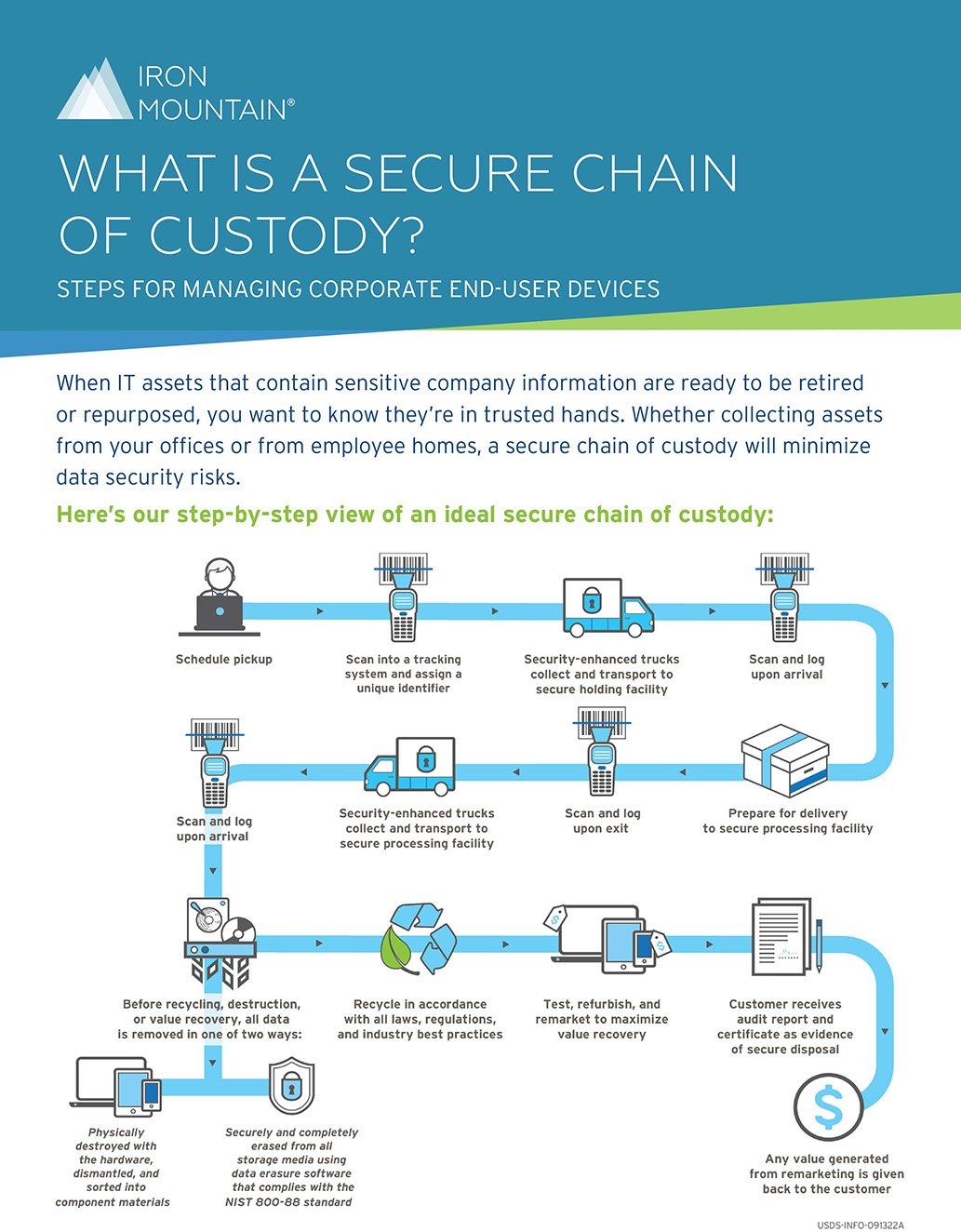
You should also be able to track your assets from the moment a contractor takes possession until the assets are successfully sold or disposed of. Real-time tracking insures against the risk of equipment disappearing during the transportation or decommissioning process.
Processing facilities should be equipped with redundant fire prevention, power, HVAC, and communication systems, as well as security guards, key-card entry, and video surveillance coverage.
With so much at risk during asset retirement, it makes sense to work with a reliable and reputable provider that ensures a fully visible chain of custody, world-class data security, maximum value recovery from remarketing, and compliance with all industry and environmental laws and regulations.
Iron Mountain’s commitment to security ensures that you know the location and status of all your IT equipment, giving you valuable peace of mind during every step of the disposition process.
Get a FREE consultation today!
 Premium
Premium
